Deploying PHP 7
DPC
João Pessoa
August 26, 2016
http://talks.php.net/expotecRasmus Lerdorf
@rasmus

✔ engine improvements
- 100%+ performance gain on most real-world applications
- Lower memory usage, sometimes drastically lower
JIT?
Improve CPU cache usage
- Step 1: Decrease overall data
- Step 2: Better data locality and less indirections
- Step 3: Save the world!
- zval size reduced from 24 to 16 bytes
- Hashtable size reduced from 72 to 56 bytes
- Hashtable bucket size reduced from 72 to 32 bytes
- Immutable array optimization
$a = [];
for($i=0; $i < 100000;$i++) {
$a[] = ['abc','def','ghi','jkl','mno','pqr'];
}
echo memory_get_usage(true);
// PHP 5.x 109M
// PHP 7.0 42M no opcache
// PHP 7.0 6M with opcache enabled- New memory allocator similar to jemalloc
- Faster hashtable iteration API
- Array duplication optimization
- PCRE JIT enabled by default
- Precomputed string hashes
- Fast ZPP (ZendParseParameters) implementation
- Faster stack-allocated zvals (instead of heap)
- Optimized VM calling
- Global register variables with gcc 4.8+
- plus hundreds of micro-optimizations
HugePage support in Opcache
./configure --enable-huge-code-pagesopcache.memory_consumption=256
opcache.huge_code_pages=1% sysctl -w vm.nr_hugepages=256
% service php-fpm start
% cat /proc/meminfo | grep Huge
HugePages_Total: 256
HugePages_Free: 231
HugePages_Rsvd: 119
HugePages_Surp: 0
Hugepagesize: 2048 kBJIT?
GCC Feedback-Directed Optimization (FDO)
$ make clean
$ make -j8 prof-gen
...
$ sapi/cgi/php-cgi -T 1000 /var/www/wordpress/index.php > /dev/null
$ make prof-clean
$ make -j8 prof-use
✔ engine improvements
- 100%+ performance gain on most real-world applications
- Lower memory usage, sometimes drastically lower
✔ Exceptions on Fatals
function call_method($obj) {
$obj->method();
}
call_method(null);Fatal error: Uncaught Error: Call to a member function method() on null in file:2
Stack trace:
#0 file(4): call_method(NULL)
#1 {main}
thrown in file on line 2try {
call_method(null);
} catch (Error $e) {
echo "Caught Exception: {$e->getMessage()}\n";
}Caught Exception: Call to a member function method() on nullPHP 7 Exception Hierarchy
- Throwable
- ➥ Exception implements Throwable
- ➥ Error implements Throwable
- ➥ TypeError extends Error
- ➥ ParseError extends Error
✔ Return Types
function get_config(): array {
return 42;
}
get_config();Fatal error: Uncaught TypeError: Return value of get_config() must be
of the type array, integer returned in file:2
Stack trace:
#0 file(4): get_config()
#1 {main}
thrown in file on line 2✔ Coercive Scalar Types
function logmsg(string $msg, int $level, float $severity) {
var_dump($msg); // string(1) "1"
var_dump($level); // int(2)
var_dump($severity); // float(3)
}
logmsg(1, "2.5 bananas", 3);Notice: A non well formed numeric value encountered in file on line 2✔ Strict Scalar Types
declare(strict_types=1);
...
logmsg(1, "2.5", 3);Fatal error: Uncaught TypeError: Argument 1 passed to logmsg() must be of the
type string, integer given, called in file on line 7 and defined in file:3
Stack trace:
#0 file(7): logmsg(1, '2.5', 3)
#1 {main}
thrown in file on line 2✔ Anonymous Classes
return new class($controller) implements Page {
public function __construct($controller) {
/* ... */
}
/* ... */
};
class MyObject extends MyStuff {
public function getInterface() {
return new class implements MyInterface {
/* ... */
};
}
}✔ Coalesce Operator
$a = NULL;
$b = 0;
$c = 2;
echo $a ?? $b; // 0
echo $c ?? $b; // 2
echo $a ?? $b ?? $c; // 0
echo $a ?? $x ?? $c; // 2✔ Spaceship Operator

function cmp_php5($a, $b) {
return ($a < $b) ? -1 : (($a >$b) ? 1 : 0);
}
function cmp_php7($a, $b) {
return $a <=> $b;
}✔ Removal of many deprecated features
(Your PHP4 code will break!)
- ext/ereg (use ext/pcre instead)
- preg_replace() eval modifier (use preg_replace_callback() instead)
- ext/mysql (use ext/mysqli or ext/pdo_mysql instead)
- Assignment of new by reference
- Scoped calls of non-static methods from incompatible $this context
- dl() in php-fpm
- set_magic_quotes_runtime() and magic_quotes_runtime()
- set_socket_blocking() (use stream_set_blocking() instead)
- mcrypt_generic_end() (use mcrypt_generic_deinit() instead)
- mcrypt_ecb, mcrypt_cbc, mcrypt_cfb and mcrypt_ofb
(use mcrypt_encrypt() and mcrypt_decrypt() instead)
- datefmt_set_timezone_id() and IntlDateFormatter::setTimeZoneID()
(use datefmt_set_timezone() or IntlDateFormatter::setTimeZone() instead)
- xsl.security_prefs (use XsltProcessor::setSecurityPrefs() instead)
- iconv.input_encoding, iconv.output_encoding, iconv.internal_encoding,
mbstring.http_input, mbstring.http_output and mbstring.internal_encoding
(use php.input_encoding, php.internal_encoding and php.output_encoding instead)
- $is_dst parameter of the mktime() and gmmktime() functions
- # style comments in ini files (use ; style comments instead)
- String category names in setlocale() (use LC_* constants instead)
- Unsafe curl file uploads (use CurlFile instead)
- PDO::PGSQL_ATTR_DISABLE_NATIVE_PREPARED_STATEMENT driver option
(use PDO::ATTR_EMULATE_PREPARES instead)
- CN_match and SNI_server_name stream context option (use peer_name instead)✔ New reserved words:
- bool
- int
- float
- string
- null
- false
- true
- resource
- object
- mixed
- numeric
✔ 64-bit integer support on Windows
✔ Cleanup edge-case integer overflow/underflow
✔ Support for strings with length >= 2^31 bytes in 64 bit builds.
✔ Parse error on invalid numeric literals
$mask = 0855; // Parse error: Invalid numeric literal✔ Uniform variable syntax
// left-to-right
$this->$belongs_to['column']
// vs.
$this->{$belongs_to['column']}
// support missing combinations of operations
$foo()['bar']()
[$obj1, $obj2][0]->prop
getStr(){0}
// support nested ::
$foo['bar']::$baz
$foo::$bar::$baz
$foo->bar()::baz()
// support nested ()
foo()()
$foo->bar()()
Foo::bar()()
$foo()()
// support operations on arbitrary (...) expressions
(...)['foo']
(...)->foo
(...)->foo()
(...)::$foo
(...)::foo()
(...)()
// two more practical examples for the last point
(function() { ... })()
($obj->closure)()
// support all operations on dereferencable scalars
// (not very useful)
"string"->toLower()
[$obj, 'method']()
'Foo'::$bar✔ Unicode Codepoint Escape Syntax
echo "\u{202E}Right-to-left text";
echo " \u{26BD}";Right-to-left text ⚽
✔ ICU IntlChar class added to intl extension
✔ CSPRNG
$int = random_int(-500, 500);
$bytes = random_bytes(10);
var_dump( $int );
var_dump( bin2hex($bytes) );int(348) string(20) "9576ce9260bcaa4509b5"
Top-5 Things that might bite you
For the full list see
Left-to-right semantics for complicated expressions
$$foo['bar']['baz'] // interpreted as ($$foo)['bar']['baz']
$foo->$bar['baz'] // interpreted as ($foo->$bar)['baz']
$foo->$bar['baz']() // interpreted as ($foo->$bar)['baz']()
Foo::$bar['baz']() // interpreted as (Foo::$bar)['baz']()To restore the previous behaviour add explicit curly braces:
${$foo['bar']['baz']}
$foo->{$bar['baz']}
$foo->{$bar['baz']}()
Foo::{$bar['baz']}()Detection: phan or unit test failures
Removed support for /e (PREG_REPLACE_EVAL) modifier
echo preg_replace('/:-:(.*?):-:/e', '$this->pres->\\1', $text);Change to:
echo preg_replace_callback(
'/:-:(.*?):-:/',
function($matches) {
return $this->pres->{$matches[1]}; // Careful!
},
$text);Detection: grep, warnings in logs or unit test failures
$HTTP_RAW_POST_DATA global removed
if (empty($GLOBALS['HTTP_RAW_POST_DATA']) &&
strpos($_SERVER['CONTENT_TYPE'], 'www-form-urlencoded') === false) {
$GLOBALS['HTTP_RAW_POST_DATA'] = file_get_contents("php://input");
}Detection: grep, warnings in logs or unit test failures
session.lazy_write enabled by default
session.lazy_write = 0Detection: Can cause out-of-band session read timing issues
Invalid octal literals now produce a parse error
echo 05678; // PHP 5.x outputs 375Parse error: Invalid numeric literal in file.php on line 2
Detecting parse errors is easy: php -l
Let's deploy it!
Atomic
No performance hit
- No restarts
- No LB removal
- No thundering herd
- Cache reuse
Must be able to serve two versions of the site concurrently!
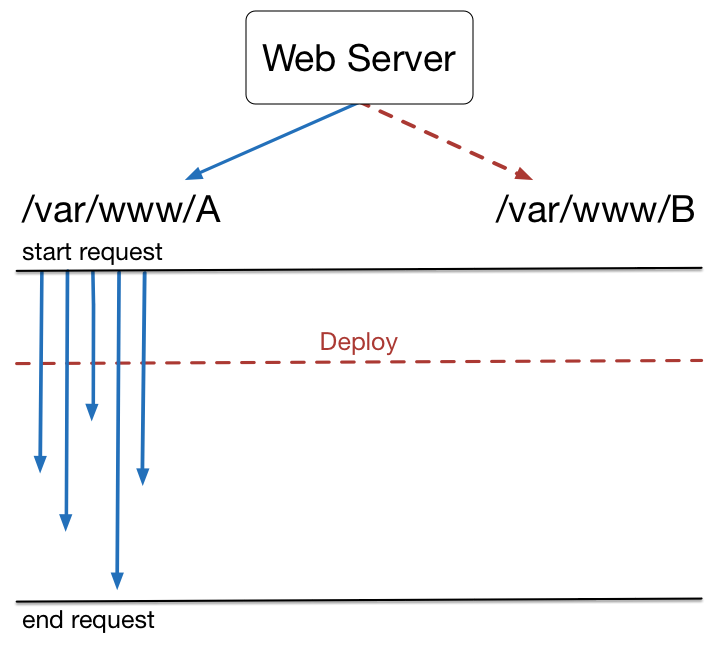
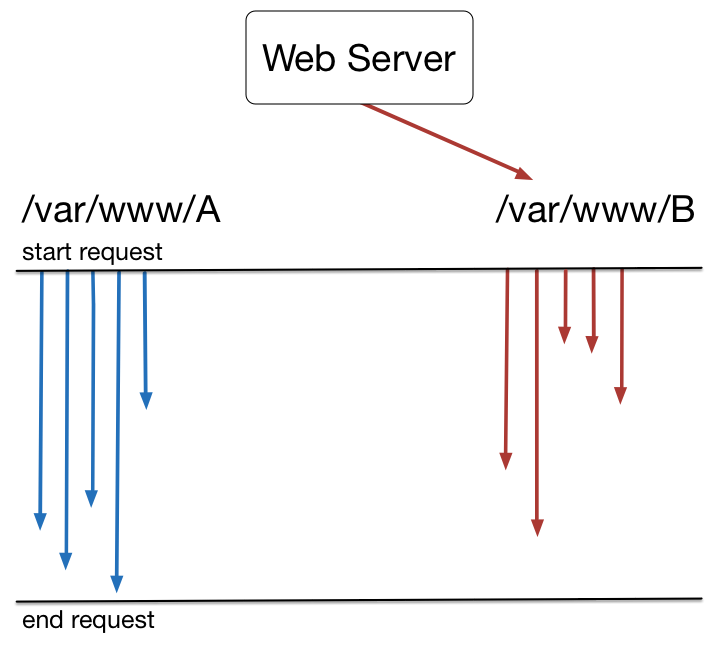
Requests that begin on DocumentRoot A must finish on A
Set the DocumentRoot to symlink target!
Easy with nginx
fastcgi_param DOCUMENT_ROOT $realpath_rootApache
Avoid hardcoding full paths
Watch your include_path setting
incpath extension can resolve your include_path for you
Version all static assets
DB Schema changes need special care
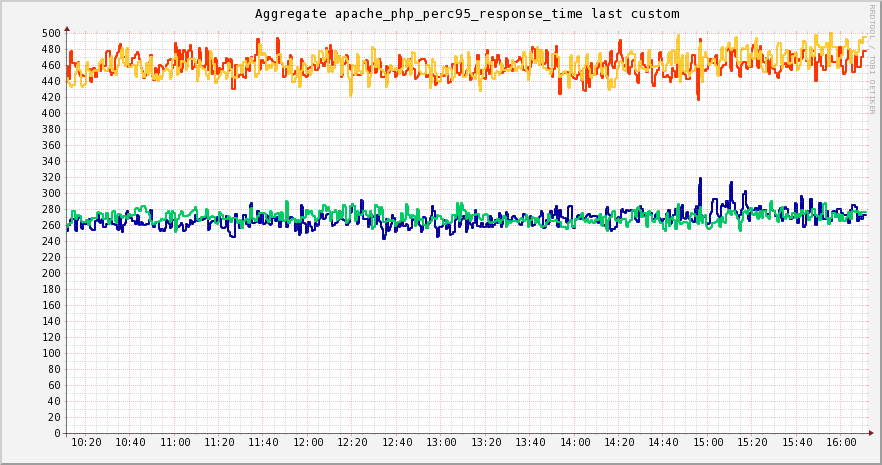
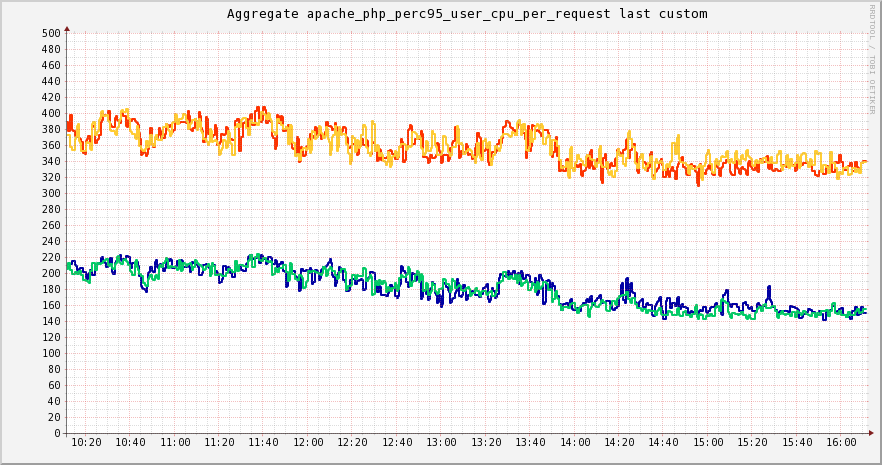
PHP 7 in production
PHP 7.1
✔ void return type
function should_return_nothing(): void {
return 1; // Fatal error: A void function must not return a value
}✔ Nullable types
function answer(int $a, ?int $b): ?int {
if($a > $b) return $a;
else return null;
}✔ Iterable pseudo-type
function foo(iterable $iterable) {
foreach ($iterable as $value) {
// ...
}
}
function bar(): iterable {
return [1, 2, 3];
}✔ Negative string offsets
$str='abcdef';
var_dump($str[-2]); // => string(1) "e"✔ List keys
list($first, $second, $third) = [1, 2, 3];
[$first, $second, $third] = [1, 2, 3];✔ Warn about invalid strings in arithmetic
$numberOfApples = "10 apples" + "5 pears";Notice: A non well formed numeric string encountered in example.php on line 2
Notice: A non well formed numeric string encountered in example.php on line 2✔ Class constant visibility
class Token {
// Constants default to public
const PUBLIC_CONST = 0;
private const PRIVATE_CONST = 0;
protected const PROTECTED_CONST = 0;
public const PUBLIC_CONST_TWO = 0;✔ Things that may break your code
- new 'void' and 'iterable' keywords
- rand() and srand() are now aliased to mt_rand() and mt_srand()
- Calling a function with too few args is now an Error instead of a Warning
- Dropped support for sslv2 streams
- Dropped support for mcrypt
Thank You
Report Bugs
Useful bug reports, please!